Tokenization is not a new vocabulary. In 2010, VISA and PCI successively released best practice guides for tokenizing data in accounts. Because of its closed application in the industry, it can be said to be “not ignorant”, but with the rapid payment of innovation Development, tokenization has once again become the focus of the industry. EMVCo launched the Payment Tokenization framework in March 2014 to promote the application and promotion of payment markers by developing globally accepted standards. This article will start with the problem, basic framework and application scenarios solved by the payment mark, and share with the reader through the analysis of related content.
I. Overview
Taking into account security and credibility and user convenience is a unique feature of the payment industry, and innovation cannot be abandoned at the same time. "Tokenization" can be rapidly developed and applied precisely because it solves sensitive information protection problems and completely transparent to users, making it easier for users to accept and use. To avoid confusion, "Tokenization" is defined as tokenization in conjunction with the actual application and working mechanism of the specification. There are two potential weaknesses to implementing data protection using traditional forms of encryption: the reversibility of encryption results and the complexity of key management. Different from the encryption scheme, tokenization is to protect sensitive information in the form of data substitution. Not only can an attacker not obtain the original data through reversible methods, but the format and structure of the substitute value can be exactly the same as the original data. To reduce the impact on business and applications.
Second, the potential weakness of the existing encryption method
Ensuring the legality of a transaction requires three levels of certification steps, one is the cardholder's certification (ensuring that the cardholder is the person), the second is card authentication (preventing the fake card), and the third is the legal voucher for the transaction (preventing Transaction refusal). But regardless of the type of transaction, the card number-based payment system, the delivery and storage of the card number still provides room for transaction fraud:
(1) Face-to-face card transactions
Due to the characteristics of magnetic stripe cards being easily copied and unauthenticated, risk events such as transaction fraud and card side recording seriously affect the normal use of bank cards. The EMV standard realizes the dynamic authentication of cards and terminals by developing a global security framework for chip cards and terminals, ensuring the security of the acceptance process; however, after the authentication, the subsequent transaction links still do not effectively protect the account sensitive information, such as :
· In the authorization, the request data is sent by the terminal to the acquiring institution or the issuing bank.
· Authorization data is sent to the recycling agency or merchant system
(2) Online cardless transactions
Innovative payment based on the Internet ecology brings convenience and convenience to users, but most of the innovative payment is basically through the card number and the corresponding sensitive information (validity period, CV2) to complete the transaction authentication. The risks are mainly reflected in:
· How to ensure that users connect to legitimate businesses
· How to verify legally authorized users
· How to send card data to merchants through a secure channel
· How to ensure the secure transmission of data between network devices
· How to ensure the non-repudiation of legitimate transactions
(3) Retaining transaction data
In order to meet the needs of value-added services such as marketing and data analysis, merchants or acquirers often store transaction data and even some sensitive data after the transaction authorization is completed. According to statistics from authoritative organizations, 92% of data breaches are caused by vulnerabilities at the application and system layers, so the protection of these key links also needs attention.
Third, the development and application of payment tokenization technology
How to solve the above problems, while eliminating sensitive data and realizing transaction authentication, as far as possible to ensure compatibility with the existing payment system is the starting point and core idea of the design of the tokenization scheme. The development of tokenization is mainly divided into two phases:
The first phase is the non-payment mark proposed by VISA and PCI (a set of values instead of PAN, which can be encrypted), such as FirstData and Cybersource for merchants to provide a tokenized acquiring solution; The lack of versatility and interoperability in the environment limits the promotion of the program.
The second stage is the payment mark proposed by EMV; the biggest feature of the program is to use Token to participate in the entire authorized transaction process, and to ensure the versatility as much as possible, thus solving the risk problem based on the card number.
(I) A brief analysis of the EMV tokenization framework
The EMV tokenization framework defines the system architecture (as shown below)
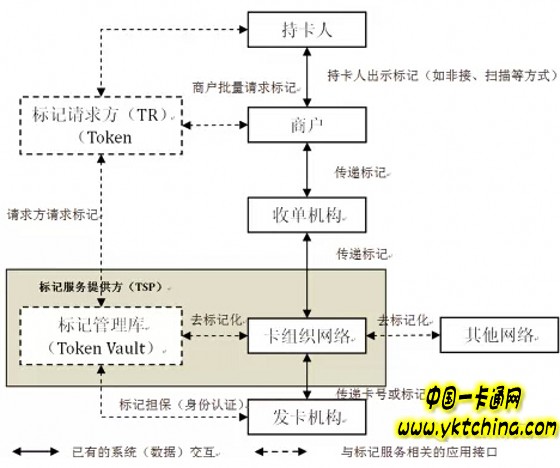
The framework describes the main roles and relationships in the existing payment industry and adds two roles, Tag Requestor (TR) and Tagged Service Provider (TSP), to provide tagging services to cardholders and merchants.